In an era where digital transactions and online interactions have become an integral part of our everyday lives, the dawn of blockchain technology marks a significant turning point in how we perceive and trust information. While the promise of decentralization, transparency, and immutability captivates innovators and investors alike, the underlying security of blockchain systems remains a pressing concern. “Fortifying the Future: Unraveling Blockchain Security Essentials” invites readers on a journey through the intricate landscape of blockchain security, exploring the essential principles and practices that safeguard this revolutionary technology. As we delve into the multifaceted layers of protection—from smart contract vulnerabilities to consensus mechanisms—our aim is to illuminate the challenges and solutions that will shape the future of secure blockchain applications. Join us as we decode the complexities of this digital fortress and explore the vital strategies needed to fortify the foundations of trust in an increasingly interconnected world.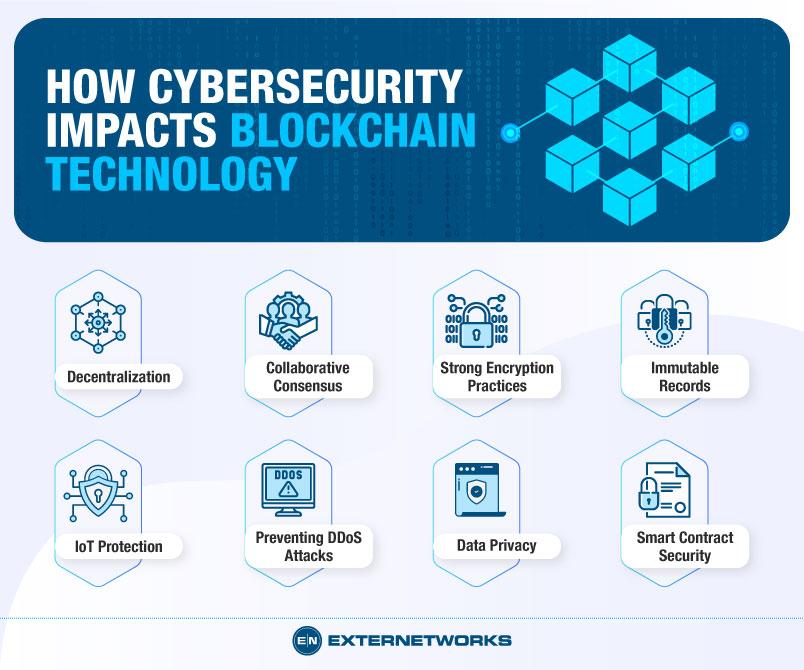
Exploring the Foundations of Blockchain Security Architecture
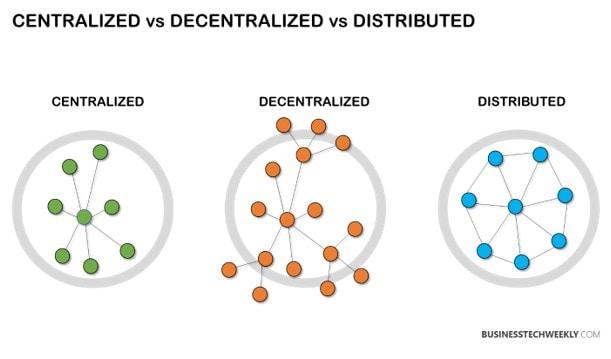
Understanding the core principles that underpin blockchain security is essential for developing robust systems that can withstand evolving threats. At the heart of this architecture is the concept of decentralization, which reduces single points of failure and enhances resilience. Embedded within blockchain technology are mechanisms such as cryptographic hashing and digital signatures that ensure data integrity and authenticity. Together, these components form a foundation that protects against unauthorized changes, making it nearly impossible for a malicious actor to alter transaction data without consensus from the network.
In addition to architectural principles, security best practices play a crucial role in fortifying blockchain systems. Organizations should prioritize regular audits and penetration testing to identify vulnerabilities within their networks. Implementing multi-signature wallets can also significantly enhance security by requiring multiple approvals before a transaction is executed. The following table summarizes key elements of an effective blockchain security strategy:
| Security Element | Description |
|---|---|
| Decentralization | Distributes data across multiple nodes to eliminate single points of failure. |
| Cryptographic Hashing | Transforms data into a fixed-size string of characters, providing secure links between blocks. |
| Digital Signatures | Ensures authenticity and integrity of transactions through cryptographic keys. |
| Multi-Signature Wallets | Requires multiple keys to authorize a transaction, adding an extra layer of security. |
| Regular Audits | Periodic evaluation of blockchain systems to identify and address vulnerabilities. |
Identifying Common Vulnerabilities in Decentralized Networks
In decentralized networks, the assurance of security isn’t just a feature—it’s a necessity. However, the very architecture that promotes decentralization can also expose these networks to vulnerabilities that are oftentimes overlooked. The absence of a central authority means that identifying and mitigating risks becomes a collective responsibility, where individual participants may be unaware of the cumulative security landscape. Key vulnerabilities include:
- Sybil Attacks: Attackers masquerade as multiple nodes to dominate the network.
- Smart Contract Flaws: Insecure coding practices can lead to exploits, enabling unauthorized access or fund diversion.
- Consensus Mechanism Exploits: Manipulating the rules governing consensus can undermine the integrity of the entire network.
- Insufficient Decentralization: If too many nodes rely on a similar source for verification, it compromises security.
To better understand these vulnerabilities, consider the comparative analysis shown below. Each vulnerability is not only unique but also demands a tailored approach in defense:
| Vulnerability | Impact | Mitigation Strategies |
|---|---|---|
| Sybil Attacks | Node manipulation and consensus disruption | Implementation of identity verification |
| Smart Contract Flaws | Unauthorized transactions and fund theft | Thorough code audits and testing |
| Consensus Mechanism Exploits | Compromise of network integrity | Diverse consensus algorithms |
| Insufficient Decentralization | Central point of failure | Encourage diverse node participation |

Implementing Best Practices for Enhanced Data Integrity
To enhance data integrity within blockchain systems, it is essential to adopt a comprehensive set of best practices that align with the decentralized nature of the technology. Implementing immutable ledgers ensures that once data is recorded, it cannot be altered or deleted, thereby preserving its authenticity. Additionally, integrating cryptographic hash functions creates a secure connection between data blocks, allowing for quick verification and safeguarding against unauthorized access. The commitment to decentralization further mitigates the risk of single points of failure, ensuring that the system remains resilient against attacks.
Organizations should also prioritize robust access control mechanisms to limit user permissions and maintain accountability. Key practices for safeguarding data include the following:
- Regular audits: Conduct periodic assessments to identify vulnerabilities and compliance issues.
- Encryption: Utilize advanced encryption techniques for data in transit and at rest.
- Backup strategies: Establish reliable backup systems to recover data in case of a breach.
Incorporating these strategies fosters a culture of data integrity, paving the way for trust and security in blockchain transactions.

Future-Proofing Blockchain Solutions Through Continuous Monitoring
In the rapidly evolving landscape of blockchain technology, the implementation of effective continuous monitoring strategies is essential for safeguarding the integrity and availability of blockchain solutions. By integrating systematic oversight into blockchain operations, organizations can proactively identify vulnerabilities, conduct risk assessments, and enhance the resilience of their systems. This approach not only helps in understanding real-time performance but also fosters a culture of security awareness among stakeholders, ensuring that everyone involved is attuned to potential threats and best practices.
Continuous monitoring enables organizations to employ advanced analytics to track transactions, audit smart contracts, and scrutinize user behaviors. Key components of a robust monitoring strategy include:
- Real-time Alerts: Immediate notifications for suspicious activities allow for swift intervention.
- Performance Metrics: Regularly analyzing system performance helps in optimizing configurations and improving efficiency.
- Compliance Checks: Ensuring adherence to regulatory requirements minimizes legal risks.
By fostering a proactive monitoring environment, stakeholders can be equipped to respond adeptly to emerging threats, ensuring the long-term viability and trustworthiness of blockchain solutions.
In Conclusion
as we stand on the brink of a technological revolution driven by blockchain, understanding and implementing robust security measures is paramount. The intricate web of decentralized networks presents both opportunity and vulnerability. By delving into the essentials of blockchain security—whether it’s through encryption, consensus mechanisms, or user education—we can fortify our digital future against the myriad of threats that loom in the shadows.
As we embark on this journey, let us remain vigilant and proactive. The tools and strategies discussed serve not just as protective measures, but as the foundation upon which a secure and prosperous blockchain ecosystem can thrive. With collaboration and innovation at the forefront, we possess the power to shape a safe digital landscape, ensuring that the benefits of blockchain technology can be fully realized. Ultimately, fortifying the future requires not just understanding, but a commitment to safeguarding the principles of transparency, trust, and integrity that are inherent to this groundbreaking technology. Together, we can unlock the full potential of blockchain while securing its legacy for generations to come.



