In an era where digital landscapes continuously evolve, the quest for security has surged to the forefront of technological innovation. As we traverse through the complexities of data breaches, cyber threats, and unauthorized access, one revolutionary solution has emerged as a beacon of hope: blockchain technology. Often celebrated for its role in powering cryptocurrencies, blockchain’s potential extends far beyond the financial realm, promising to reshape how we protect our vital information. In this article, we delve into the cutting-edge innovations paving the way for enhanced blockchain security, exploring how these advancements not only fortify our digital future but also redefine trust in an increasingly interconnected world. Join us as we unravel the intricate web of security measures and innovative strategies that are setting a new standard for safeguarding our digital assets.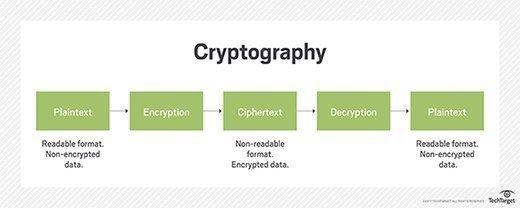
Enhancing Data Integrity through Advanced Cryptographic Techniques
In the landscape of digital transactions, data integrity has emerged as a critical concern, prompting the exploration of sophisticated cryptographic techniques. These techniques safeguard against unauthorized access and instill trust in the authenticity of shared information. By leveraging asymmetric encryption and hash functions, organizations can ensure that data remains untampered throughout its lifecycle. Notably, the use of digital signatures not only confirms the identity of senders but also guarantees that any alterations to the data can be immediately detected, fortifying the very foundation of secure communications.
Furthermore, the integration of zero-knowledge proofs into blockchain mechanisms allows parties to validate transactions without revealing sensitive data. This cryptographic method empowers users to retain control over their information while enhancing privacy. Consider the following complementary technologies that can elevate data integrity:
| Cryptographic Technique | Purpose |
|---|---|
| Asymmetric Encryption | Ensures secure data transmission between parties. |
| Hash Functions | Validates data integrity by producing unique outputs. |
| Digital Signatures | Authenticates identities and confirms data integrity. |
| Zero-Knowledge Proofs | Enables transaction validation without revealing data. |
Decentralized Identity Solutions and Their Role in Securing Personal Information
In an era where data breaches and identity theft are rampant, decentralized identity solutions emerge as a beacon of hope, promising enhanced security for personal information. By leveraging blockchain technology, these solutions empower individuals to control their identity without relying on centralized authorities. This shift not only reduces vulnerabilities associated with traditional identity management but also places the onus of data protection back into the hands of the user. Key benefits of decentralized identity solutions include:
- User Control: Individuals manage their own data and selectively share it with trusted parties.
- Enhanced Security: Data is encrypted and distributed across a network, making unauthorized access extremely difficult.
- Privacy Preservation: Users can remain anonymous while still proving their identity when required.
Moreover, decentralized identity frameworks often utilize smart contracts that further automate and secure transactions. These programmable agreements execute predetermined conditions, ensuring that identities are only verified and released following strict security protocols. A comparison of traditional versus decentralized approaches highlights the significant advantages of this innovative methodology:
| Feature | Traditional Identity Solutions | Decentralized Identity Solutions |
|---|---|---|
| Data Ownership | Centralized | Decentralized |
| Security Level | Moderate | High |
| Risk of Data Breach | High | Low |
| User Control | Limited | Full |

Smart Contract Audits: Best Practices for Mitigating Vulnerabilities
As the adoption of blockchain technology continues to grow, so does the necessity for rigorous smart contract audits to uncover potential vulnerabilities before they can be exploited. A proactive approach begins with a comprehensive review of the contract’s code, focusing on key areas such as logic errors, reentrancy issues, and improper access control mechanisms. Engaging with a reputable auditing firm can ensure that the code adheres to established best practices and provides a fresh perspective on potential pitfalls. Additionally, employing automated analysis tools can complement manual audits, offering an initial layer of scrutiny that helps to highlight red flags that require further investigation.
Beyond the typical auditing process, it’s crucial for developers to cultivate a culture of security awareness throughout their teams. Establishing best practices includes implementing continuous integration and delivery (CI/CD) pipelines that incorporate security checks at every stage of contract development. Regularly updating smart contracts and maintaining comprehensive documentation also plays a vital role in mitigating risks. By creating a checklist to adhere to, developers can ensure that all necessary measures are taken to enhance the security of their smart contracts:
| Best Practice | Description |
|---|---|
| Code Reviews | Conduct peer reviews for every line of code. |
| Testing | Utilize unit and integration tests to cover edge cases. |
| Documentation | Maintain detailed documentation for clarity and traceability. |
| Bug Bounty Programs | Incentivize external researchers to find vulnerabilities. |

Building Resilience: Strategies for Blockchain Network Security and Threat Mitigation
In an era where cyber threats are evolving at an unprecedented pace, the importance of robust security measures for blockchain networks cannot be overstated. Implementing layered security protocols serves as a foundational strategy, where multiple defenses are established to create a resilient infrastructure. Key approaches include:
- Multisignature wallets: Requiring multiple signatures for transactions significantly reduces the risk of unauthorized access.
- Regular audits: Conducting thorough security audits helps identify vulnerabilities before they can be exploited.
- Smart contract optimization: Rigorous testing and verification of smart contracts can prevent execution errors that may lead to security breaches.
Moreover, the integration of monitoring tools and real-time threat analysis enhances the ability to respond swiftly to potential risks. By employing advanced AI-driven analytics, network administrators can detect anomalies and flag suspicious activities in real-time, allowing for proactive intervention. A collaborative approach among stakeholders within the blockchain ecosystem is essential; sharing intelligence related to threat vectors can empower organizations to strengthen their defenses collectively. The following table showcases emerging technologies that are shaping the landscape of blockchain network security:
| Technology | Benefit |
|---|---|
| Quantum Cryptography | Unbreakable encryption methods enhancing data security. |
| Decentralized Identity Solutions | Empowering users with control over their personal data. |
| Distributed Ledger Technologies | Increasing transparency and traceability across transactions. |
Key Takeaways
As we stand at the crossroads of technology and security, the innovations emerging from the realm of blockchain offer a beacon of hope for a more secure digital future. This exploration into the advancements of blockchain security underscores not only the potential of this transformative technology but also the imperative for ongoing vigilance and adaptability in the face of evolving threats.
The journey does not end here; rather, it is a continual process of learning, adapting, and fortifying. As we harness the power of decentralization, cryptography, and consensus mechanisms, we inch closer to a paradigm where trust is not merely an abstract concept but a foundational element woven into the very fabric of our digital interactions.
In an era where data breaches and cyber threats loom large, the innovations discussed in this article are not just enhancements; they are essential defenses in the ever-evolving landscape of cybersecurity. As we move forward, it will be crucial for stakeholders—be they developers, businesses, or users—to collaborate and share insights, paving the way for a resilient blockchain ecosystem.
In closing, the path to fortified security is paved with creativity, diligence, and foresight. By embracing these innovations and remaining proactive in our approaches, we can collectively navigate the complexities of tomorrow’s digital sphere, ensuring that the future is not only bright but secure. The confluence of technology and trust lies ahead—let us stride confidently into this new era.



